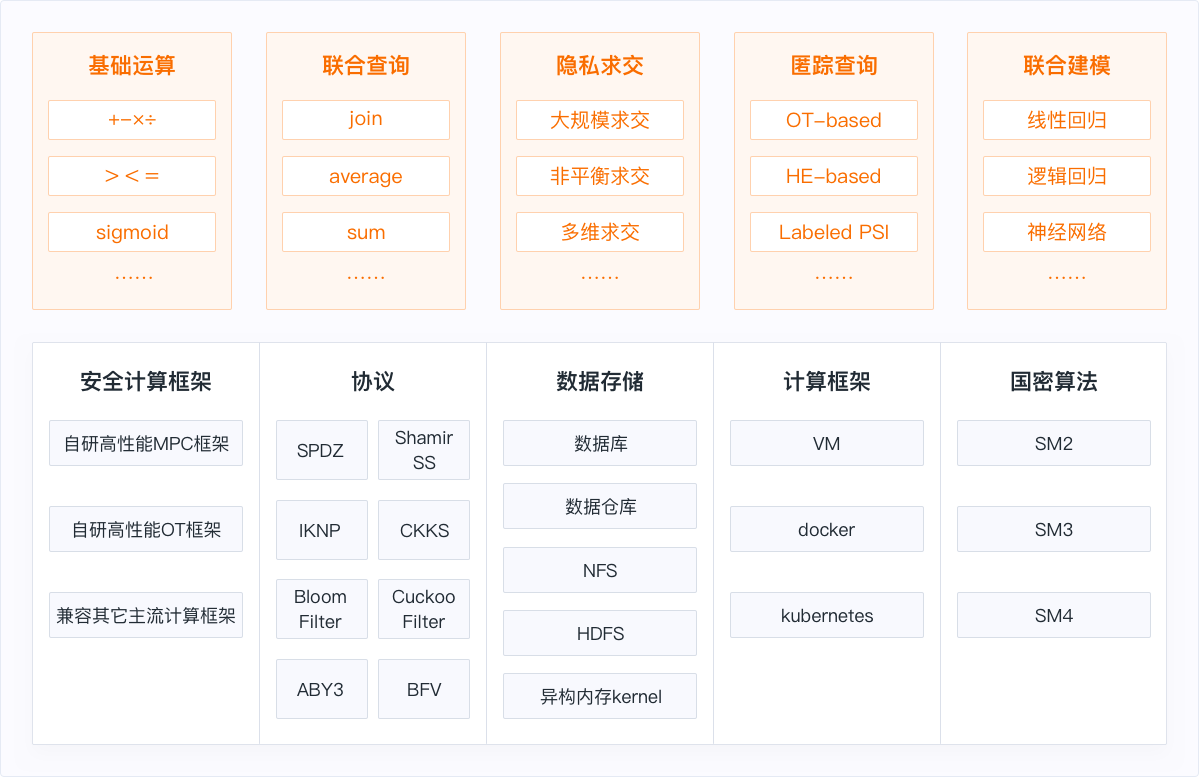
Arithmetic operation
The basic operator of statistical operation is provided, and the algorithm performance is optimized and upgraded. The calculation time of ten-thousand-level floating point number multiplication is millisecond

The basic operator of statistical operation is provided, and the algorithm performance is optimized and upgraded. The calculation time of ten-thousand-level floating point number multiplication is millisecond

On the premise that the original data is not leaked, it provides SQL mode continuous table query, including mean, sum and other operations. It only takes tens of seconds for millions of database continuous table query to calculate the mean

On the premise of not revealing the content of the set of both sides, the intersection data of both sides is calculated. The non-intersection data is not disclosed, and it only takes a few minutes to cross the data of hundreds of millions

In the case of not divulging the purpose of the query, not divulging additional data, users can successfully query information, million level database, million level indistinguishable, can respond in a few seconds in a timely manner

The underlying implementation of each operator uses a variety of secret sharing, homomorphic encryption and careless transmission protocols including SPDZ, ABY3, CKKS, IKNP, KKRT and so on. While ensuring security, the most advanced SOTA protocol with the highest recognition is adopted

The security of joint query, joint statistics, joint modeling and other tasks is reduced to mathematically difficult problems to ensure the security in the scheme and protocol

Computations can be submitted in JSON format. Computations can be performed using expressions and SQL and can be quickly deployed in public cloud, private, or offline environments

The product is completely domestic and researched, and the underlying symmetric/asymmetric encryption mode of each cryptography protocol supports the use of state secret algorithm, compatible with mainstream databases and data services